Common Google XSS
When I was searching for a vulnerability in google DNS from Google Cloud, I came across this article by Julien Ahrens. The article is about an SSRF vulnerability in the Google website https://toolbox.googleapps.com, so I started researching this site.
Simple research ⇾ XSS
The site has many apps, all of them are listed inside the robots.txt file:
#apps-toolbox
User-Agent: *
Allow: /apps/main
Allow: /apps/browserinfo
Allow: /apps/checkmx
Allow: /apps/dig
Allow: /apps/har_analyzer
Allow: /apps/loganalyzer
Allow: /apps/loggershark
Allow: /apps/messageheader
Allow: /apps/recovery
Allow: /apps/useragent
Allow: /apps/other_tools
Allow: /apps/encode_decode
Allow: /apps/screen_recorder
Disallow: *
Most of the tools are accessible from the /apps/main menu, however, the recovery app (at /apps/recovery) isn’t.
From a simple search in google I see the recovery app has these sub-pages:
recovery/domain_in_use
recovery/form
recovery/ownership
All of which receive many parameters from the query string in URL (parameters in {url}?parm1=1¶m2=2...): visit_id, user, domain, email and some more.
In google search I also spotted a result that has Verify that you own example.com title, with this link : https://toolbox.googleapps.com/apps/recovery/ownership?domain=example.com&email=email@example.com&case=45500368&continue=/apps/recovery/...
The server apparently just verifies that the email matches the domain, then presents a page with some thank you text and a continue button:
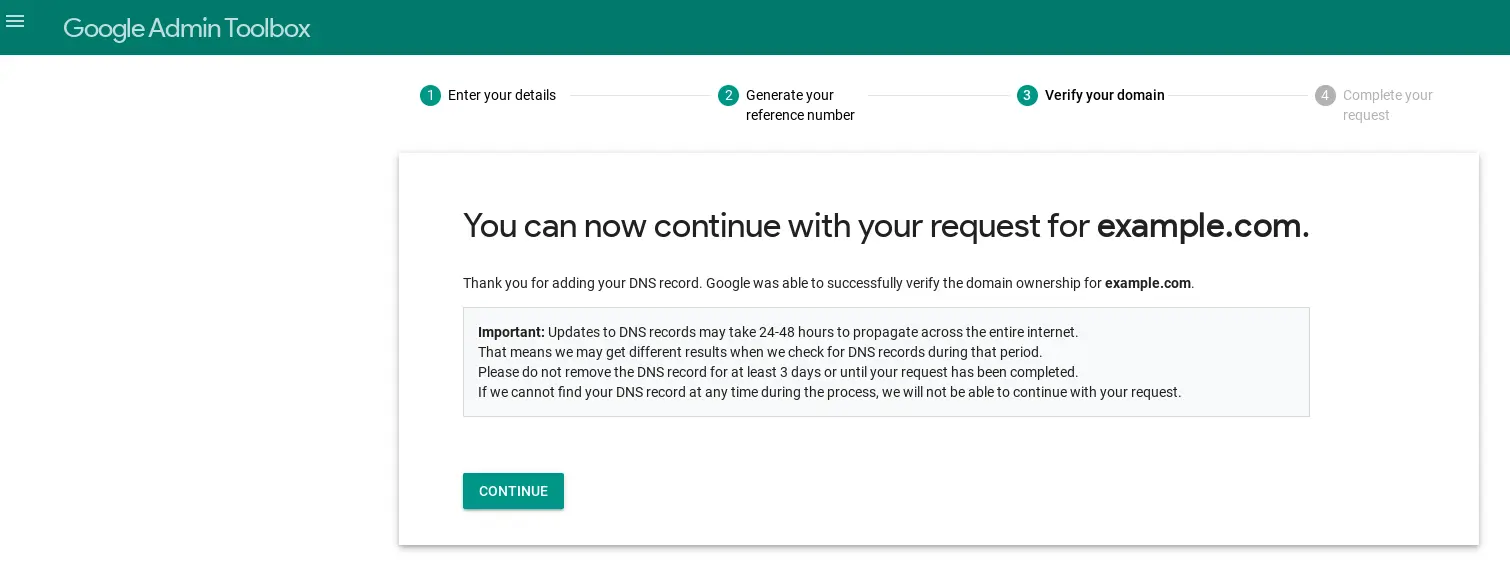
And the link in the continue button, was … you guessed it: just taken from the continue URL parameter.
So I tried placing there continue=javascript:alert(document.domain), and… It works!
The site didn’t use any CSP, or any protection at all. So I also could send and receive data from external sites: (e.g. continue=javascript:fetch(%27https://api.ipify.org?format=json%27).then(response=%3Eresponse.text()).then(data=%3E{alert(data);%20}), which alerts the user public ip). I reported it to Google.
Reward
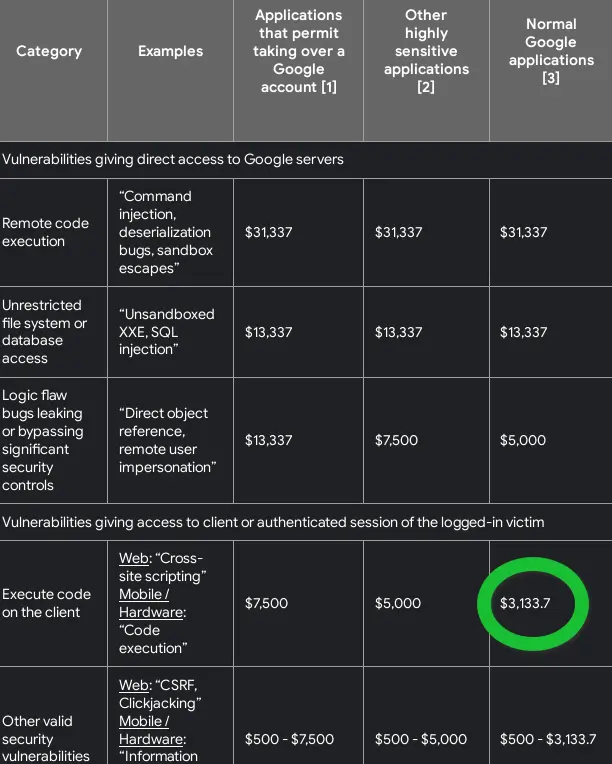
Since this is an XSS, and its on a normal Google application, it falls into the 3133$ square in google rewards. Therefore, I got more than twice than I got to both parental control bypasses (googles secret browsers) combined.
I name this article “Common” because it’s really an openredirect->xss by the book. No thinking is required, just trying to change random parameters on URLs.
Comments: (You can also Comment directly to this discussions )